In the telecommunication industry, fraud attacks are common. Moreover, it is an unsettling topic that demands the attention of all VoIP software, solutions, and service providers. Typically, VoIP fraud involves hackers exploiting vulnerabilities to gain unauthorized access to the system or service. Specifically, they get unauthorized access to premium communication services. As a result, attackers can use these premium services unfairly and cause financial losses. This financial loss is imposed on someone, which is either an end user or the service provider. Even if you use the best VoIP billing solution, you cannot track the attacker. Moreover, you cannot do anything once your system is attacked to recover the loss.
Definitely, you can get over the attacks after detecting them by taking security steps. However, what is lost is lost. Therefore, it is necessary to take precautionary steps to avoid being a victim of these fraud and hack attacks.
Transform your billing system for enhanced performance with our tailored VoIP billing solution.
It is challenging to get rid of VoIP fraud completely. However, acquiring the right knowledge can considerably reduce the likelihood of falling victim to such attacks. According to a famous proverb, education emerges as a potent defense against this evolving threat in the business landscape. In the past year, the VoIP industry faced a loss of US $ 50 billion due to VoIP fraud. This and other recent evidence indicate a clear surge in VoIP fraud instances. In short, it is necessary to stay informed and well prepared to mitigate potential risks.
Certainly, as mentioned earlier, it is not possible to avoid VoIP fraud completely. However, you can definitely detect these attacks at the early stages with the right software and vigilant monitoring. Moreover, timely detection and right action can become imperative to safeguard against potential financial losses and protect the integrity of communication systems.
1. What is VoIP Fraud?
Simply put, VoIP fraud refers to deceiving activities that involve unauthorized access and use of VoIP services for making voice calls over the internet. Moreover, this access is to the premium services to increase the intensity of attack.
Generally, fraudsters use different approaches to identify and exploit vulnerabilities within VoIP software solutions to gain illicit access to premium communication services. Fundamentally, VoIP fraud occurs when individuals or entities employ unapproved methods to access and utilize paid VoIP services without proper authorization. VoIP fraud can result in financial losses for service providers or end-users. Therefore, all types of VoIP fraud are major concerns for the provider and its customers.
For example, if you are using an open source VoIP billing software solution that is not updated for a long time. Then, it will have several open windows and backdoors to let attackers get in and invade the system to cause several losses.
2. Major Types of VoIP Fraud Attacks
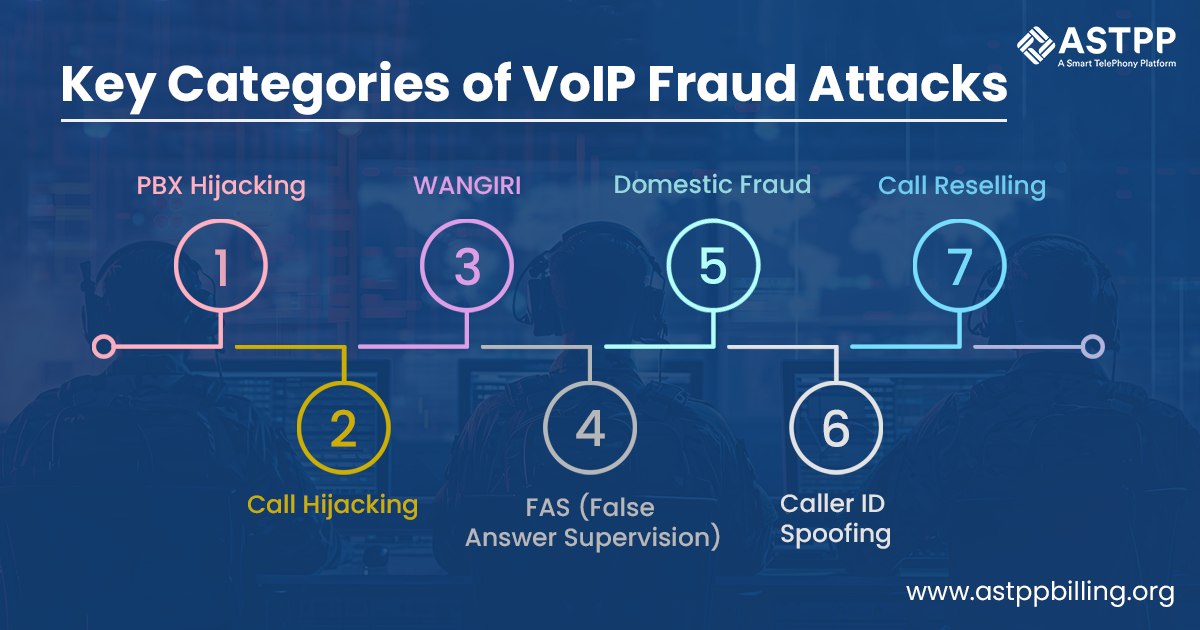
There are several types of fraud attacks that you need to know. Knowing these fraud attacks can help you identify them and take the required steps.
2.1 PBX Hijacking
It is a process of unauthorized access to a PBX (Private Branch Exchange) solution. Moreover, it can also involve unfair access to a business phone system for an IP PBX solution user. Moreover, attackers establish different configurations. For example, they set up call forwarding or dial-through functions. As a result, these calls are directed to high cost destinations and keep increasing the bills for the users, which will reflect in the user’s bills generated by a VoIP billing solution.
Secondly, hackers use an IP-based source to avoid detection. Moreover, they initiate numerous calls to the PBX, which will redirect them to specified expensive destinations. Thirdly, PBX hijacking is used along with IRSF (International Revenue Share Fraud) or call hijacking. Certainly, IRSF is a common approach for call reselling fraud.
Retail customers may receive invoices for unauthorized calls from a VoIP billing solution company. As a result, retail service providers face the challenge of crediting stolen traffic to the compromised PBX owner. As a result, they need to face financial losses and even reputation damage.
2.2 Call Hijacking
This attack involves a process of intentionally rerouting a number of calls to unauthorized destinations. For example, all calls from network A are intended to reach network C. Moreover, this call distribution will happen through operator B to an announcement server playing a recorded message. This is a classic scenario of call hijacking.
Certainly, in this fraudulent attack, the legitimately called party is never reached. However, it still allows transit operator B to charge all calls at the committed rate and it allows operator B to incur a 100% profit margin. The transit operator attracts substantial traffic by offering low prices. As a result, they enjoy an increase in traffic for the operator engaging in call hijacking. Conversely, end customers keep encountering recorded messages and they may initiate additional calls. As a result, it contributes to the transit operator’s gains in this exploitative practice.
2.3 WANGIRI
This attack happened for the first time in Japan. Therefore, it has the Japanese name WANGIRI, which means one (ring) and cut. In other words, it is a type of missed call, which simply sends a single call ring. Therefore, it is also known as a missed call fraud campaign. Moreover, this fraud attack can combine CLI (Caller ID) spoofing, IRSF (International Revenue Share Fraud), and spamming.
Fundamentally, an attacker sends numerous calls to the targeted end user, telecom operator, or VoIP service provider. Moreover, these calls are abruptly terminated after a few rings. Definitely, it is a characteristic of VoIP phone scams. Nevertheless, the targeted operator or end user will receive a missed call notification with a falsified CLI linked to a Premium Rate Service. As is human nature, the recipient will give a callback, which may lead to a false destination. Moreover, the call can also lead to adult-oriented content. Moreover, the customer will get charged premium rates as configured in the VoIP billing software. This can lead to major financial losses.
2.4 FAS (False Answer Supervision)
It is a misleading signaling method. Specifically, this method is used for falsely indicating call establishment. As a result, it charges for longer call durations than the actual connection time. Moreover, FAS includes situations where calls are not genuinely connected. Therefore, it increases the charges for call set up time. Furthermore, this attacking technique is employed in conjunction with call hijacking. Thus, a false call connection indication is given. As a result, it will increase charges for incomplete calls and call set up time, even when the called party is unreachable.
2.5 Domestic Fraud
It is quite identical to International Revenue Share Fraud (IRSF). Fundamentally, it involves the artificial generation of traffic towards premium rate number services. Moreover, fraudsters compromise the telephony assets of your customers by redirecting the traffic to premium rate services (PRNs). Generally, the attacker will have an arrangement with the PRN network owner. Therefore, attackers receive a portion of the illegitimate revenue generated through this deceptive practice.
2.6 Caller ID Spoofing
Undoubtedly, one of the major concerns of several countries is caller ID spoofing and robocalls. In fact, the increasing volume of these attacks has mandated legal authorities to take actions that can combat these attacks. For example, the FCC in the USA has mandated the implementation of a STIR/SHAKEN certificate implementation for a business if it wants to provide VoIP or communication services in the USA.
Caller ID spoofing is a deceptive way to alter the caller ID that is used to trick the end user into completing malicious intents. For example, the attacker will alter the caller ID to someone the end user knows such as a friend or a legal department representative. Subsequently, the attacker will trick the customer and receive some sensitive information. As a result, major financial loss will occur. Moreover, it can lead to several other consequences.
2.7 Call Reselling
It is the practice of traffic diversion to trick customers. Basically, a wholesaler strategically includes a destination on their pricing list at a significantly reduced rate compared to the standard price. Therefore, this route receives high traffic because it will appear as a more cost effective option. To avoid the impracticality of terminating traffic at a much lower standard price, the wholesaler resorts to hacking a PBX and utilizing it as a switch. In this type of attack, the wholesaler incurs no costs, and the associated traffic charges are billed to the customer.
These are the top seven types of fraud attacks that commonly happen in the VoIP industry. However, this is not it. There are several other types of VoIP fraud that make it difficult to stay completely protected.
3. Top Software Tools to Avoid Fraud and Hack Attacks

As discussed earlier, it is impossible to avoid fraud attacks completely. However, you can implement the right tools and infrastructure to protect your VoIP network, business, and clients. Let us discuss the major software tools that you must implement.
STIR/SHAKEN Certificate
If you are doing business in the USA, you must implement STIR/SHAKEN as mandated by the FCC regulations. Moreover, in France, this certificate is mandatory. It is a digital signature, encryption, and verification method that verifies the legitimacy of caller ID.
Fraud Detection and Management Software
The best VoIP billing solution company, ASTPP has developed an enterprise module for fraud detection and management. Fundamentally, this solution allows service providers to create different rules. These rules define the threshold of legitimate use of the system and service. Moreover, this solution allows service providers to define actions in case anyone violates this legitimate use of the software or service.
We have a recommended reading for you that shares the top trending fraud attacks in the global telecom industry. This article shares a brief of the top 4 trending VoIP attacks that you must have knowledge of.
For example, they can define that from a predefined country, only 800 minutes (about 13 and a half hours) of calls are permissible during a week. Firstly, if someone reaches this limit within a day or two, it should give a warning alert. Secondly, if someone crosses this limit, then his or her access to the system must automatically be suspended. Moreover, the system must send notifications to the admin and technical engineer to deal with the system.
SBC (Session Border Controller) System
It is a security solution that provides session level security. Moreover, it inspects all data packets and voice traffic at the border of the VoIP network. It acts as a border element between different IP networks to consolidate security. In addition to security, it provides interoperability, transcoding, and several other features.
4. Top Tips to Protect your Business from VoIP Fraud Attacks
Invest in Technology
It is necessary to use the best software for your business. Moreover, you must implement VoIP security mechanisms to protect your VoIP network. Furthermore, you need to upgrade software applications regularly with each version release.
Follow Regulatory Enforcements
Different governments implement different security checks and rules. For example, the FCC has mandated the implementation of the STIR/SHAKEN protocol. All these regulatory enforcements are defined based on the existing threats and security attacks. Therefore, it is always good to follow these regulatory enforcements correctly.
Monitor Traffic and Other Signals
Even if you have implemented the best software and security tools, you must get the best live call monitoring system. Luckily, security tools will have inbuilt real time call monitoring features. This will help you monitor traffic and take immediate action.
Concluding Note
In conclusion, VoIP fraud and malicious attacks are common and unavoidable in this industry. Moreover, these attacks can cause major consequences for VoIP users. Therefore, it is necessary to invest in the right technology, best practices, and software tools that can help you keep your system protected.
We provide the best VoIP billing solution, as well as security tools to help you safeguard your VoIP network and business. To discuss how we can help you consolidate your business and its security from VoIP attacks, contact us.





