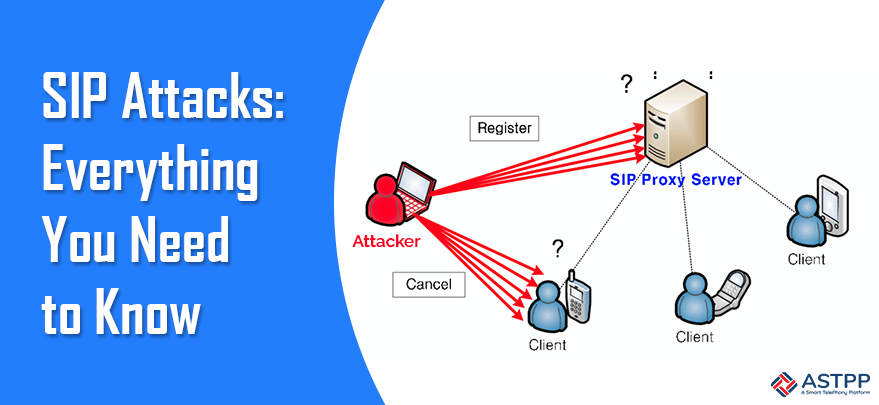
Each ITSP and VoIP business, from a startup or an established player, knows the seriousness of SIP attacks. SIP attacks can make a VoIP business owner bankrupt. Having cold feet by reading this is not a solution. The best solution is to know about the common SIP attacks and how you can safeguard yourself and your business from these SIP attacks.
To help you deal with these attacks, we are going to share 3 major SIP attacks, which are commonly faced by many VoIP businesses. Also, we will share more details about the solution to keep your system and business protected from these SIP attacks.
1. DOS (Denial of Service)
- The most common attack on the SIP systems like class 4 Softswitch is DOS attacks.
- The attacker suddenly starts sending illegitimate traffic in massive volume to drain out the system capacity and other resources.
- Tracing the number also gets near to impossible as usually, the separation between data and signaling channels is not available.
Why is it dangerous?
-
- It drains out all resources and all this can happen within a short time. It means even if your real customers are not using your services, they are getting used by the attackers. You will need to pay for the used resources and services such as carriers. This can make you bankrupt if your system or team fails to identify this attack at the earliest possible and take the required action to stop it. Within a few hours, it can send a flood of calls, so before you can realize the situation, you get into big trouble.
Everything You Need to Know About SIP Attacks Awaits!
- On the other hand, as this SIP attack blocks all resources, your actual customers do not receive the service they want. This would further result in increased customer dissatisfaction and the following consequences would be there waiting for you.
2. DDOS (Distributed Denial of Service)
- The attackers use a network of computers and other interconnected devices to send unusual traffic to the targeted network, system, or server.
- Each of these systems used in attacking a system, like an infrastructure set up for multi tenant IP PBX solution, is called bots or zombies.
- The whole network of bots used to attack the system is called a botnet.
- The botnet clog up the system or server, so genuine users cannot access it.
- The sent traffic denies the services to be provided to customers and multiple systems get used in carrying out this attack, thus, it is referred to as distributed denial of service.
- There are 7 different types of DDOS attacks that can overwhelm a system at a specific layer out of seven layers to disturb the operational flow and exhaust the resources of the target.
Why is it dangerous?
- It can drain out the resources in use and make the system completely fail.
- It has the same business brand and economy damaging effects as DOS attacks have. It is more dangerous and difficult to control SIP attacks.
3. Toll frauds
- One of the most common attacks that happen to the VoIP systems is toll fraud. Almost all VoIP businesses have faced this attack and often it goes unnoticed on an immediate basis.
- In this type of SIP attack, the attackers break through the vulnerable part of the VoIP system to enter into the system and sell resources to a third party.
- For example, if you use DID numbering solution to run your DID number business, the attacker may break through the system and sell your DID numbers without your consciousness. In case, if you are using a calling card solution to offer calling card services, then the attacker can use the call minutes to let third-party customers or businesses carry out calling using your system. In this case, the third party pays to the attacker.
- This attack is also known as time theft and dial-through fraud.
Why is it dangerous?
- This type of attack often goes unnoticed because the calls made from genuine business numbers. It often looks like your own customers are using your services. It means for a long time, the attackers can keep making money by using your resources.
- The obvious threat is your resources stay in use, but you do not get paid for the same. It clearly results in major financial loss.
What is the solution?
There are multiple solutions to stay protected from these common SIP attacks. We are going to share one commonly used along with the recommended solution.
Manual monitoring:
- This is the most commonly used solution to keep the system protected from these attacks.
- Admin and technical team keep monitoring live statistics to make sure there are no unusual activities.
- They also check reports to see if there are any phishing activities at a regular interval.
- This is not a recommended solution because often SIP attacks start subtly and it becomes tough to control or very late when it actually comes to the attention of the admin and technical team.
Fraud detection solution:
- It is an automated solution that is built specifically to identify fraudulent activities and SIP attacks automatically. Not only this, but this software can also take action to block attacks then and there to save the business from recoverable losses.
- The fraud detection system sends the notification and alerts on an immediate basis to the concerned team members as soon as something unusual is identified by the system, so they can delve deeper and take further action, if required.
- As detecting SIP attacks and fraud activities is completely automated, this system assures as sooner as something unusual happens, the required actions are taken.
- The advanced fraud detection solution also gives several options to set rules to make security more consolidated.
Using a reliable fraud detection system is the ultimate solution to deal with SIP attacks and fraud attempts.
ASTPP, A Smart TelePhony Platform, offers several VoIP solutions as well as add-ons. One of the add-ons offered to ASTPP users is fraud detection. This add-on has the most advanced features to safeguard any VoIP business. Contact us for a free demo and a free trial.