Since July 1, 2021, the Federal Communications Commission (FCC) has blocked the voice traffic of all providers that failed to implement the STIR/SHAKEN certificate. This shows the importance of the STIR/SHAKEN solution if you want to do voice business in the USA. FCC had taken this call due to the increasing nuisance of robocalls. Moreover, more than 40% of these calls were fraud calls with caller ID spoofing. Millions of robocalls were generated and a majority of them were targeting consumers to trick them with a spoofed caller ID. Therefore, implementing a security mechanism to protect the interests of users has become a necessity for the government. As a result, the authority introduced STIR/SHAKEN. Moreover, it is made mandatory for all voice service providers.
Upgrade your security now!Harness the power of STIR/SHAKEN for unparalleled protection.
The main agenda of the STIR SHAKEN protocol is to reduce as many fraudulent calls as possible. Moreover, it also helps in improving the overall customer experience and win trust, too. Therefore, it is important for all voice or VoIP service providers to learn about STIR/SHAKEN and use it effectively. It helps in following compliance. Moreover, it benefits you in becoming a trusted brand in the network and market. Therefore, even if you don’t provide voice services in the USA, you must use this security tool to protect your business and customers.
To give you a detailed insight into this topic, we will cover all vital details on this subject matter.
You must be excited to learn more about this interesting topic. So, without any further delays, let’s get into the details.
1. Understanding STIR/SHAKEN
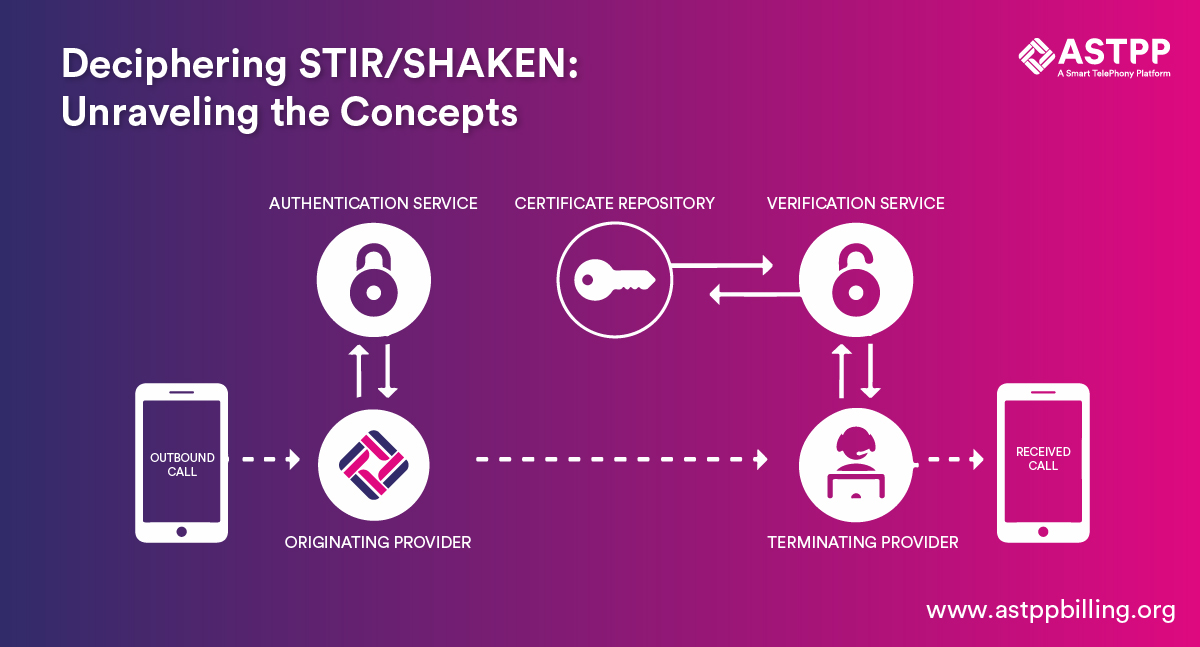
STIR (Secure Telephone Identity Revisited) and SHAKEN (Signature-based Handling of Asserted information using toKENs) are two different concepts. Certainly, they are useful together to build a secure system to protect customers from fraudulent calls and similar threats.
STIR/SHAKEN is a framework to enforce security in the voice network. This security methodology uses a digital certificate. This certificate works on the cryptography method with a public key. The intent of implementing the STIR/SHAKEN certificate is to give a hint of the call to the receiver. It indicates whether the call is trusted or not. It is accurate in displaying the possible caller ID spoofing to the receiver. As a result, a more secure ecosystem of voice communication is possible to build with the right usage of this technology.
2. Understanding Caller ID Spoofing and Robocalls
Some fraudsters use caller ID spoofing techniques to temper the caller ID before dialing a number. At the receiving end, the caller ID displays as someone from the authority, legal department, or someone they already know. As a result, a fraudster, it becomes very easy for them to trick an end user. Fraudsters will easily retrieve sensitive information from end users such as their credit card details. They can even trick them into stealing money along with the information.
For example, using caller ID spoofing, a fraudster connects with the consumer as an authority from the taxation department. The fraudster tricks the customer and asks them to pay the due tax. The call recipient gets tricked and pays the tax. Here the recipient is not paying the tax, but actually losing money to a fraudster.
Robocall is another scam that helps scammers to loot customers. A machine generates Robocalls automatically to deliver a prerecorded voice message. The scammers may use tools like voice blast software or similar to blast voice call campaigns. If you attend the call, spammers add your number to the database. Your number will become their favorite. As a result, you will receive more fraud calls, robocalls, and caller ID spoofing based calls.
STIR/SHAKEN solution helps in securing a network completely from caller ID spoofing. Moreover, it also helps customers of a voice service provider to identify possible fraud calls with an alert.
You must read our blog post covering the steps to combat spoofed calls using STIR/SHAKEN, here.
3. Working Methodology of STIR/SHAKEN
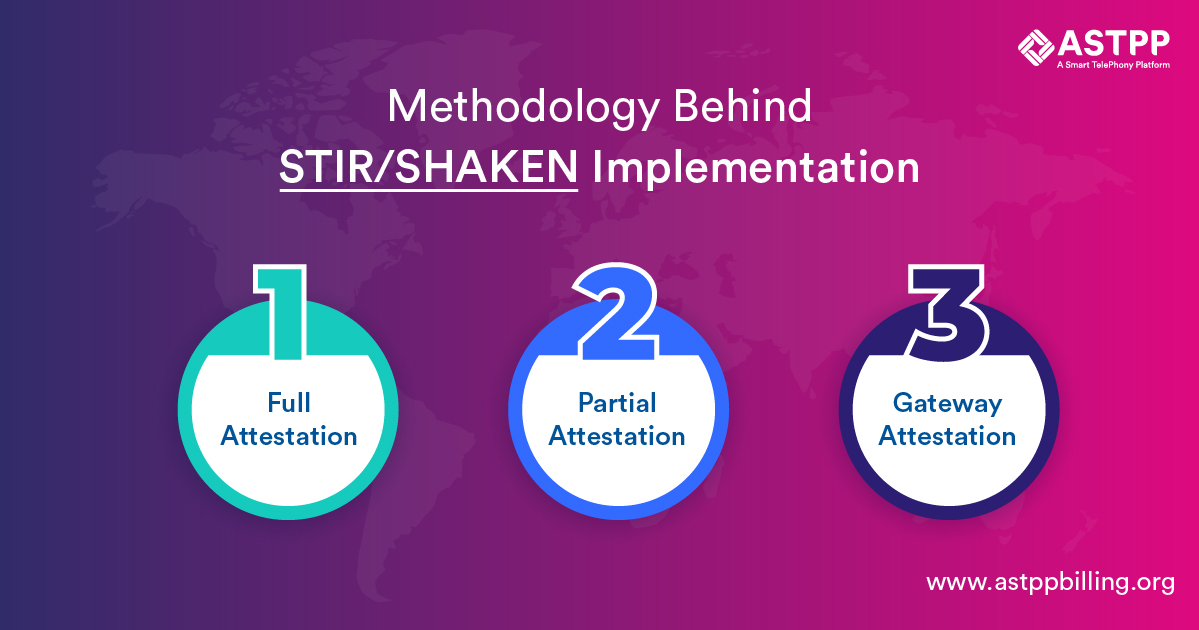
STIR/SHAKEN solution is an effective tool to combat caller ID spoofing, robocalls, and other fraudulent calls. This is necessary as per FCC, as well as the TRACED Act to control robocalls and verify and authenticate caller ID and that also at the network level.
STIR/SHAKEN methodology works on Attestation methodology. There are three types of Attestation:
3.1 Full Attestation:
In this case, the voice service provider will have access to the database using which he can verify authentication of the caller ID. This is the safest method of all. Moreover, it gives more control over the whole process, too. As a result, fraud calls are completely prevented.
3.2 Partial Attestation:
As the name suggests, the voice service provider can only partially verify the user. Firstly, it can verify and authenticate call origination. However, he cannot verify the source of the call. Therefore, it cannot give complete security.
3.3 Gateway Attestation:
In this method, the voice service provider is able to authenticate the call origination, but again the source is not verified. For example, international gateway usage for calling uses gateway attestation.
STIR/SHAKEN solution will include any of this attestation depending on the STIR/SHAKEN certification included by the service provider. Let’s understand the complete methodology in a stepwise manner:
The voice service provider will attach a SIP identity header to each call going out of its network. This SIP header is created by any software or algorithm. It is also known as an identity header, which will add the following information.
- Calling number
- Recipient number
- Attestation level
- Origination identifier and
- Current timestamp
The identity header will be circulated to the termination provider. Moreover, it will also be passed to the verification service provider.
At the receiving end, a voice service provider network will review all incoming calls entering their network. Depending on the Attestation method implemented by the provider, caller ID number, call source, and other details to authenticate the number and its source. The public key verification is done with the SHAKEN method.
The digital certificate with the public key is verified by the termination service provider.
Based on the verification process implemented by the receiving service provider, the provider will show the authentication level of the call. He can show whether the call is trusted or not.
STIR/SHAKEN certification can be implemented for free or by using the paid service. In the paid service, you get access to a bigger database to verify the caller ID.
If you are interested in implementing STIR/SHAKEN by yourself, then we have a DIY guide here. This blog post shares detailed steps to generate a certificate of STIR/SHAKEN and implement it using FreeSWITCH.
4. Major Advantages of STIR/SHAKEN
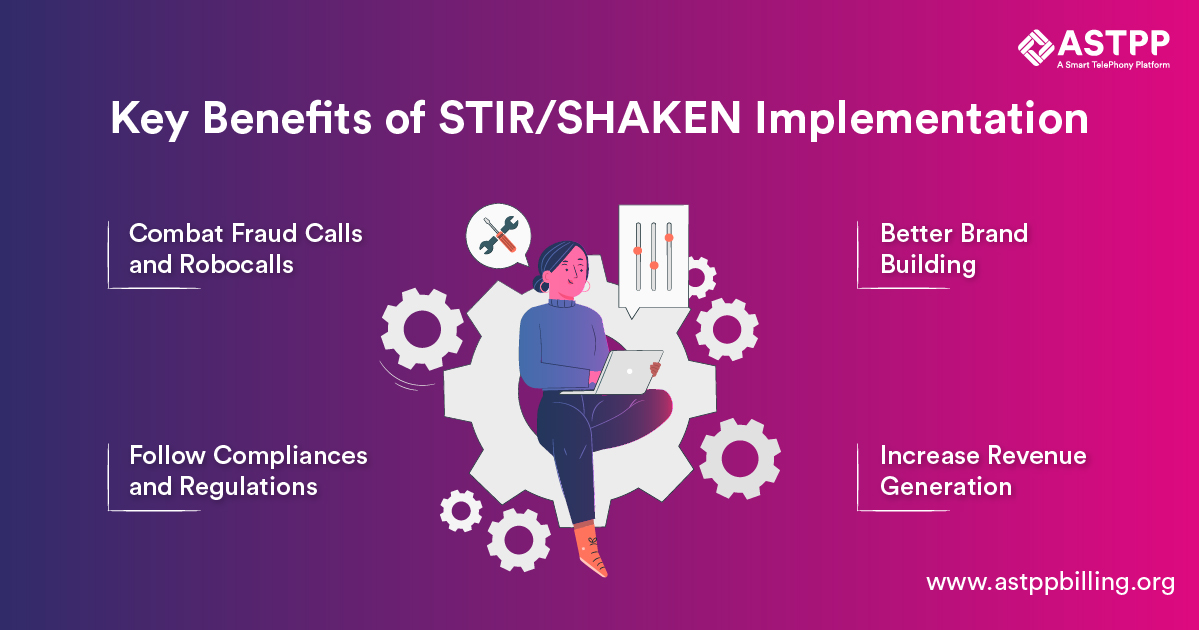
There are several advantages of implementing STIR and SHAKEN. Let’s explore the major ones.
4.1 Combat Fraud Calls and Robocalls
One of the major advantages of implementing STIR/SHAKEN solution is combating threats of fraud calls and robocalls. It gives relief to users of your services from frauds and attackers. Moreover, it helps in removing all concerns related to caller ID spoofing.
4.2 Follow Compliances and Regulations
The TRACED Act and FCC have enforced the use of the STIR/SHAKEN mechanism in the public interest. Therefore, anyone operating as a voice service provider in the USA or interested in offering voice services in America needs to implement STIR/SHAKEN. By implementing this security method, you will follow the compliances and regulations set to protect the interests of customers.
4.3 Better Brand Building
Branding is necessary in positioning business and gaining a competitive edge. Implementing STIR/SHAKEN in your network assures the security of your clients from common fraud attempts in the USA. This gives positive branding to your business. This helps in improving the numbers of your business and growth.
4.4 Increase Revenue Generation
A good reputation, security from fraud calls, and positive brand building will help your business to expand manifold. You will retain clients with good and secure services. As a result, you will maintain a positive revenue stream. Moreover, you will get new business and clients. As a result, you keep boosting your revenue generation.
5. Concluding Notes
Security has been a major concern of consumers using VoIP based communication services for many years. With advancements in technology, fraudsters have come up with several advanced techniques to trick people and steal their money. Robocalls and caller ID spoofing are two major attacks that tricked many people. As a result, authorities like the FCC and the TRACED Act identified STIR/SHAKEN as a reliable way to combat these commonly known challenges. They have mandated the implementation of STIR/SHAKEN to protect consumers from common fraud attacks.
Implementation of the STIR/SHAKEN protocol is quite easy. Even we have a guide to implement this certificate with ease. Take advantage of this security mechanism to safeguard your network, customers, and business.
ASTPP is one of the most protected platforms in the VoIP industry. Moreover, we provide a premium service for implementing STIR/SHAKEN in the network. In addition to that, we provide the required consultation to implement this certificate in your business. Furthermore, we can provide a service to implement the STIR/SHAKEN solution for your VoIP network. To discuss more about our services and offerings, contact us.





