In the VoIP industry, different types of fraud attacks happen. STIR/SHAKEN are one of the preventive measures that can help in protecting users from a type of call fraud, called call spoofing.
What is a call spoofing?
It is a form of fraud attempt made by people with malicious intent. They spoof the calling number to deceive the person that is going to receive the call. In simple words, the caller ID will be changed by the frauds, so the call receiver thinks it is a call from somebody he or she knows or someone from the government department.
Frauds use this deception method to trick people and steal their money in one way or another.
This is one of the serious issues and that is why to control it, a rule is enforced for the providers. That rule is STIR/ SHAKEN.
What is STIR/SHAKEN?
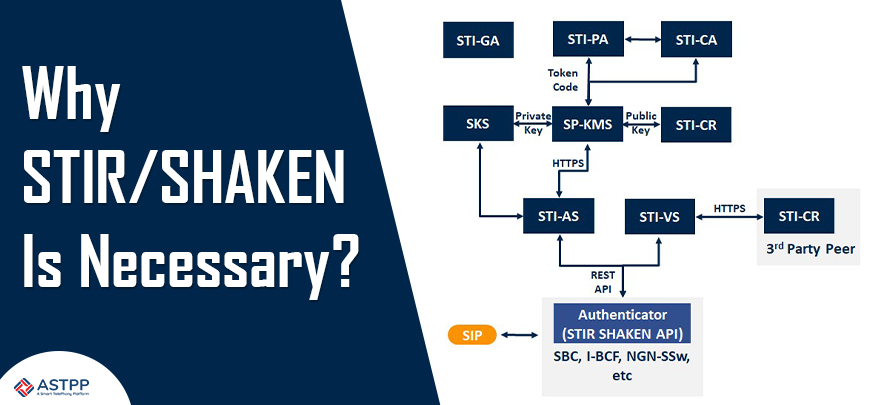
STIR stands for Secure Telephone Identity Revisited and SHAKEN stands for Signature-based Handling of Asserted Information Using tokens standards.
STIR creates the digital signature for calls that are traversing through the interconnected phone network. It has a set of protocols that are used to produce the digital signature.
On the other hand, SHAKEN defines the standards and best practices that providers need to follow to implement STIR in their networks.
STIR/ SHAKEN uses the public key cryptography technique based on a digital signature for calls, so it can be assured that all calls are protected from fraud attempts.
This is a process that can prevent robocalls and call spoofing.
How does STIR/ SHAKEN prevent call spoofing?
When a calling party initiates a call, it first goes to the carrier that offers calling services. Carrier will inspect the call number, call source, and other details to confirm the validity of the number. The service provider will define SIP (Session Initiation Protocol) identity header using the authentication service. This SIP ID header will contain attestation level, source number, destination number, current timestamp, and origination identifier.
On the other hand, the carrier at the receiving end will receive all this information along with the identity header. The service provider at the receiving end will perform the verification process using a public certificate. If at any point, the verification process fails, then the call is spoofed otherwise the call is not spoofed. In the latter case, the receiving telephony service provider will traverse the call to the called party and connect the Caller and Calle. The originating service provider will also receive the results of verification.
Why is STIR/SHAKEN required?
As per one of the statistics, more than 3 billion robocalls are made only in the USA and more than 40% of these calls are fraud attempts.
To control this type of robocall, FCC has made it mandatory for telephony service providers and carriers to implement STIR/ SHAKEN.
STIR/SHAKEN is crucial for FCC compliance and customer protection against fraud calls.
ASTPP helps providers to implement STIR/SHAKEN successfully without any roadblocks. To know more about how ASTPP can help, contact us.